Secure Active Recording – CUCM Configuration
Secure Active Recording builds on the configuration for Cisco Active Recording – see Active Recording – CUCM Configuration. This section describes the required process to follow, with the following points showing the high-level steps in the configuration process:
Create a SIP Security Profile
To be able to setup a SIP trunk as a secure trunk, a SIP Security Profile must be created. This produces a profile that can be shared across multiple SIP devices in the CUCM. This profile will only be applied to the SIP Trunk for recording.
From the drop-down menu at the top right side of the Cisco Unified Operating System Administration page, select Cisco Unified CM Administration and click Go.
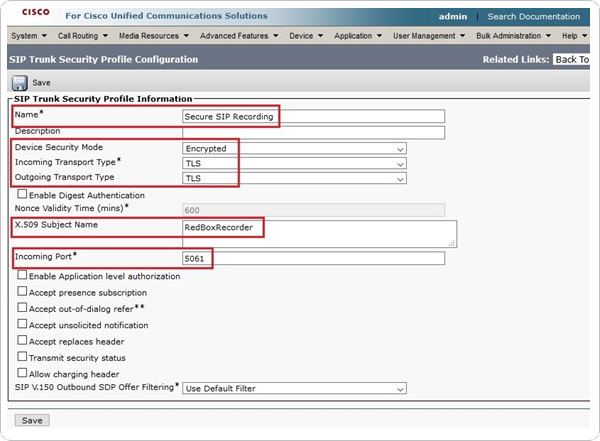
Select System > Security > SIP Trunk Security Profile and click Add New.
Create a new SIP Security Profile with:
Name – Secure SIP Recording
Device Security Mode – Encrypted
Incoming Transport Type – TLS
Ougoing Transport Type – TLS
X.509 Subject Name – RedBoxRecorder
Incoming Port – 5061
Click Save and then click Reset to confirm.
Configure the SIP Trunk for Security
The SIP Trunk must be configured to use the SIP Security Profile and treat calls as secure. When complete, the CUCM will use a secure connection to the Collector and allow encrypted calls to be recorded.
Select Device > Trunk and click on the SIP Trunk configured for recording.
Scroll down the Device Information section and click on the SRTP Allowed tick box.
Scroll down to the SIP Information section and in the Destination Port field enter 5061 and click Save.
Select System > Security > SIP Trunk Security Profile and click Save.
Verification
Start sniffing with Wireshark. Dial the route pattern for the trunk from any Cisco phone registered with the CUCM. This will cause the CUCM to send secure SIP to the Collector.
In Wireshark using the display filter tcp.port == 5061 confirm that SSL protocol is being used between the CUCM and the Collector. Confirm that there is data being exchanged. The data will be encrypted so reading it will not be possible.
Port 5061 is the secure SIP port. If there’s SSL data on it, then the CUCM and the Collector are using secure SIP.
Create a SIP Security Profile
To be able to setup a SIP trunk as a secure trunk, a SIP Security Profile must be created. This produces a profile that can be shared across multiple SIP devices in the CUCM. This profile will only be applied to the SIP Trunk for recording.
From the drop-down menu at the top right side of the Cisco Unified Operating System Administration page, select Cisco Unified CM Administration and click Go.
Select System > Security > SIP Trunk Security Profile and click Add New.
Create a new SIP Security Profile with:
Name – Secure SIP Recording
Device Security Mode – Encrypted
Incoming Transport Type – TLS
Ougoing Transport Type – TLS
X.509 Subject Name – RedBoxRecorder
Incoming Port – 5061
Click Save and then click Reset to confirm.

Configure the SIP Trunk for Security
The SIP Trunk must be configured to use the SIP Security Profile and treat calls as secure. When complete, the CUCM will use a secure connection to the Collector and allow encrypted calls to be recorded.
Select Device > Trunk and click on the SIP Trunk configured for recording.
Scroll down the Device Information section and click on the SRTP Allowed tick box.
Scroll down to the SIP Information section and in the Destination Port field enter 5061 and click Save.
Select System > Security > SIP Trunk Security Profile and click Save.
Verification
Start sniffing with Wireshark. Dial the route pattern for the trunk from any Cisco phone registered with the CUCM. This will cause the CUCM to send secure SIP to the Collector.
In Wireshark using the display filter tcp.port == 5061 confirm that SSL protocol is being used between the CUCM and the Collector. Confirm that there is data being exchanged. The data will be encrypted so reading it will not be possible.
Port 5061 is the secure SIP port. If there’s SSL data on it, then the CUCM and the Collector are using secure SIP.