Configuring OAuth2 Authentication
X‑Platform integrates OAuth2 authorization to provide an extra security layer for access to protected resources, when required.
OAuth (Open Authorization) is a standard framework for granting a user from another site or server limited access to protected information that resides on the X‑Platform Server.
X‑Platform OAuth2 authentication uses a two-tiered authorization process.
In the first tier, access to a Flow is granted via the application key for the Application being used.
In the second tier, access is granted to the external site (typically a third-party server) for the user, a process that includes both logging in and providing and returning a temporary access token.
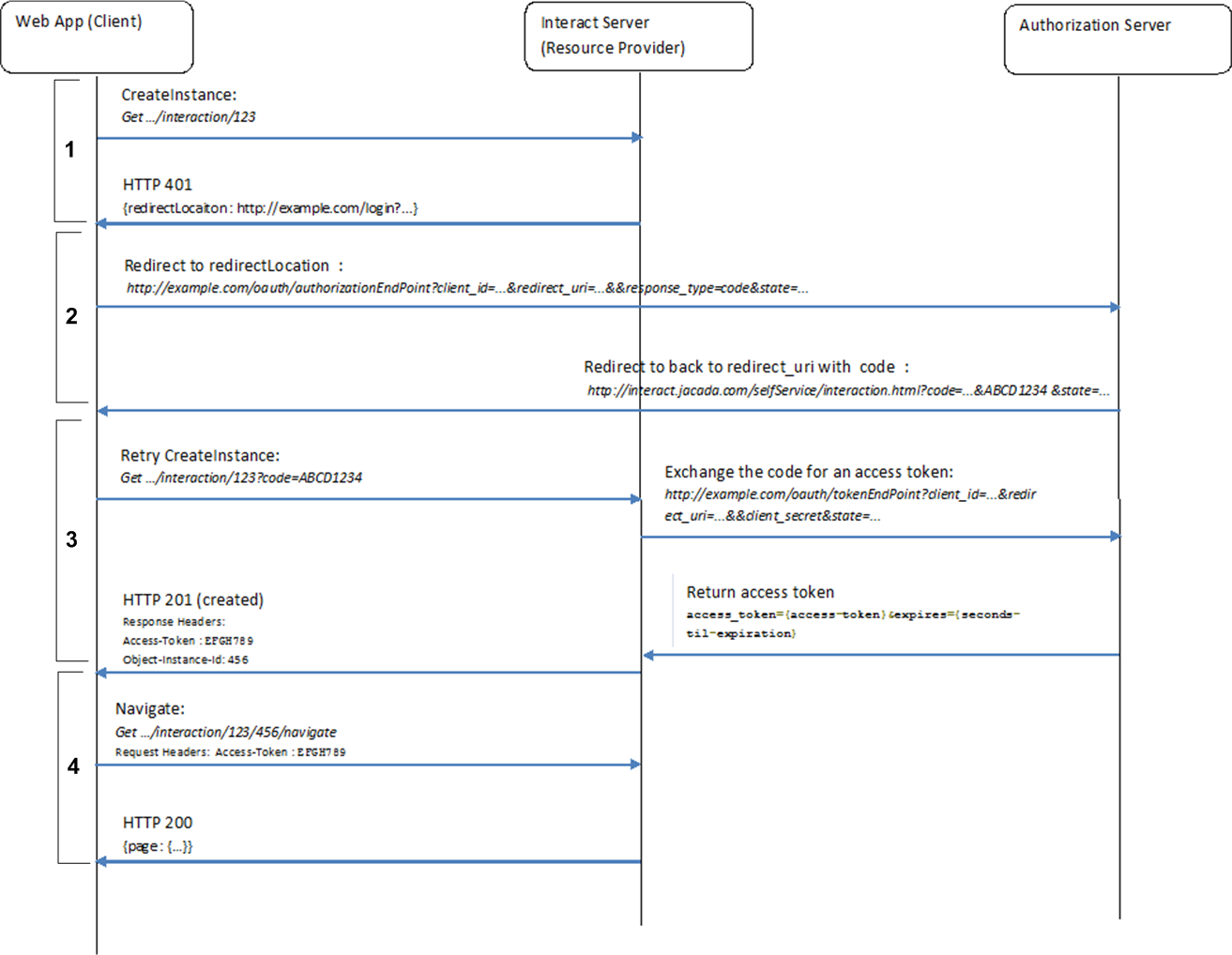
The following diagram details the full second-tier authentication flow of four phases.
 |
Phase | Process |
|---|---|
1 | The user requests access to a secured Flow, and is redirected to the Login page. |
2 | The user logs in against the authorization server, and the client is provided with an authentication code. |
3 | The client presents the code to the X‑Platform Server, and this server sends the code to the authorization server, where it is exchanged for an access token. The access token is returned to the client. NoteAt this stage, the Access Token read-only Session Variable is populated. This variable may be used, for example, in Integration Points to invoke any APIs exposed by the OAuth provider, or to retrieve specific details about the user's account. |
4 | A second request for the secured Flow (using the access token) is sent to the X‑Platform Server, and the relevant Flow is invoked for the client. |
Configuring OAuth Settings for an Application
You configure OAuth authentication for an application from the Authentication panel on the relevant Mobile or Web Application.
From the Applications page of the X-Console, click the Name link of the relevant Application. The settings tabs for the Application are displayed.
Click on the Authentication tab. The Authentication panel is displayed:
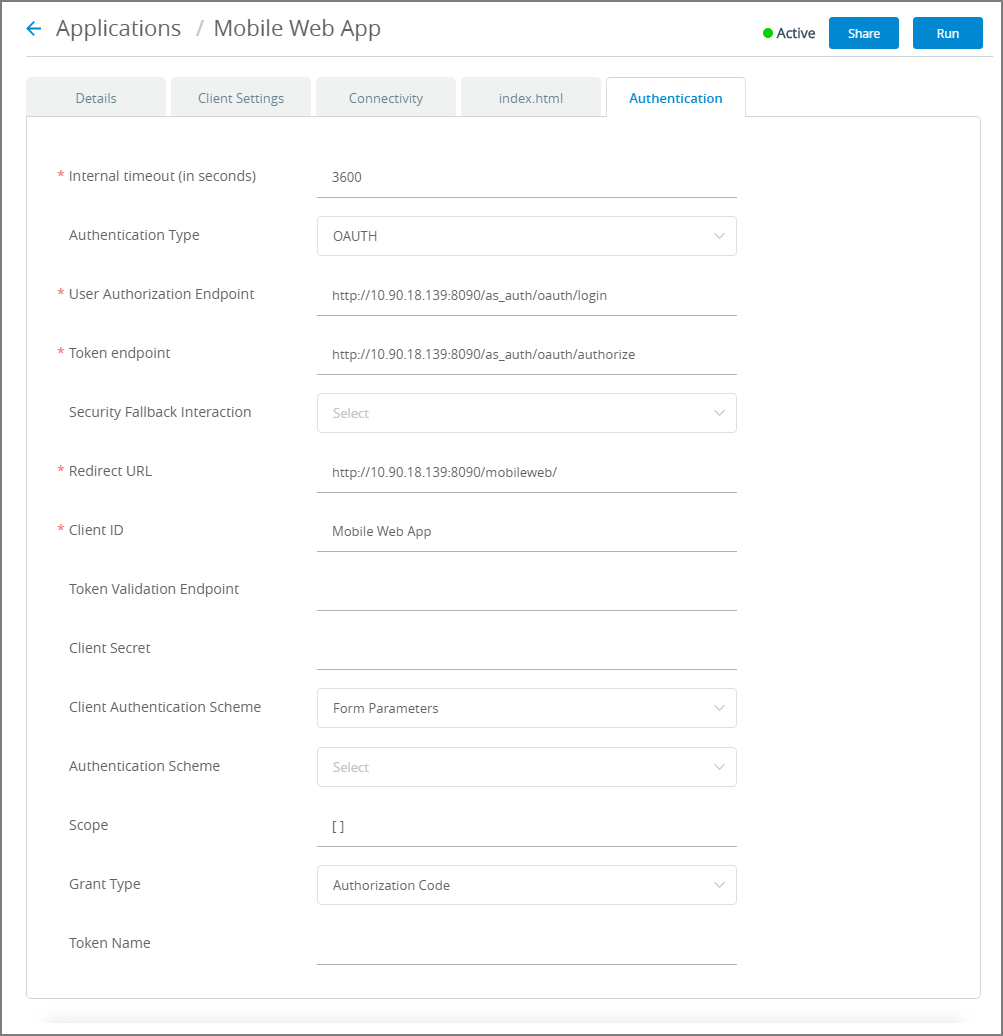
From the Authentication Type dropdown list, select the OAUTH method.
In the User Authorization Endpoint field, enter the full URL path to the Login page for the authorization server.
In the Token Endpoint field, enter the full URL path to the authorization server that is used to obtain an access token.
From the Security Fallback dropdown menu, optionally select the Flow that is presented to a user in the event that authorization to the application is not granted by the X‑Platform Server.
In the Redirect URL field, enter the location to which to return after the access token is granted.
In the Client ID field, enter the value for the 3rd party authorization server at the time of client registration.
In the Token Validation Endpoint field, enter the full URL path to the authorization server used to verify the validity of an existing access token. (This setting is not mandatory.)
Enter the additional parameters in the panel according to requirements of your OAuth authentication server.
At the lower right of the page, click Save. The new settings will be saved for the application and will become effective immediately. Note: You must save the changes you make in the Authentication Settings panel for them to be updated in the selected application.